army judge
Super Moderator

WACO, Texas (KWTX) - If you're one of the 72.2 million Americans AAA expects to travel for the 4th of July, one of the things at the top of mind should be keeping your personal devices safe.
Experts say one of the biggest culprits for stolen personal data is public Wi-Fi networks.
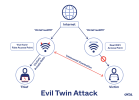
Augustin Lara, who works in cybersecurity at Texas State Technical College, says this is often due to a scam where people create a network that looks identical to a safe and trusted Wi-Fi network.
He says one of the easiest ways to combat this is to avoid accessing anything linked to your personal information while using these networks.
"For instance, everybody likes to check their bank account every now and then, right?" said Lara.
"So, say you get on the public Wi-Fi and go to log in. If the wi-fi you're using is not fully secured, if you don't see a lock at the top of your URL bar, they can potentially get your username and password."
Lara says there are ways to ensure a public connection is safe, such as using a VPN to encrypt your connection.
When in doubt, the most secure option is to link to a personal Wi-Fi hotspot.
Another potential hazard is what TSA calls "juice-jacking", a process where hackers install malware at USB ports.
So, they caution travelers to avoid plugging their phone directly into public charging stations and USB ports.
"When you connect your phone to your computer, what happens? You get that prompt on your phone," said Lara.
"Do you want to allow file sharing? Not everything is going to ask you that. Something may just skim your phone and just take all of the connections. To use this, you have to allow your file sharing for whatever reason. That's where they take your data."
If you need to charge your phone on the go, Lara recommends plugging into a wall outlet or using a personal portable charger.

Public Wi-Fi networks, phone charging stations can lead to stolen information
Augustin Lara, who works in cybersecurity at Texas State Technical College, says this is often due to a scam where people create a network that looks identical to a safe and trusted Wi-Fi network.
wifiphisher | Kali Linux Tools
Video wifiphisher Usage Examples Do not perform jamming (-nJ), create a wireless access point (-e “Free Wi-Fi”) and present a fake firmware upgrade to clients (-T firmware-upgrade). When a client connects, they a presented with a webpage to enter the PSK of their network: root@kali:~#...

What Is a Rogue Wi-Fi Attack? How Fake Networks Trick You Into Giving Up Your Data - Fidalia Networks
In this article, we’ll explain how rogue Wi-Fi attacks work, how to spot them, and what you can do to stay safe while using public networks.
